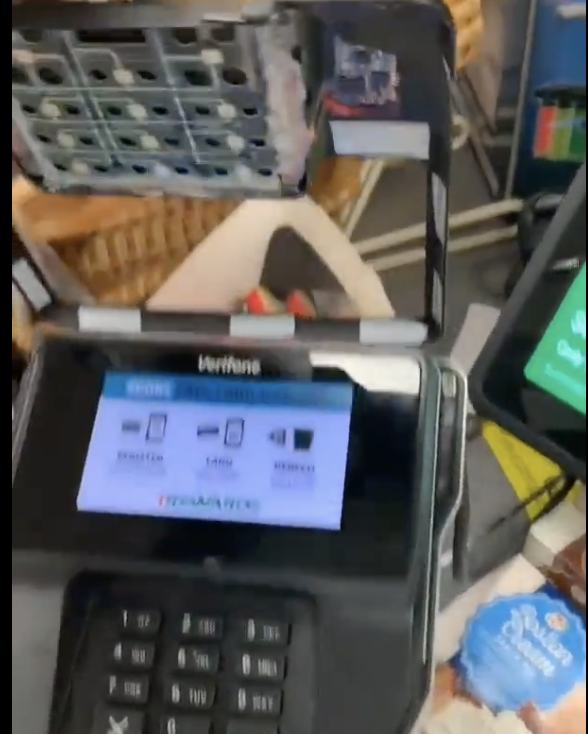
Small devices called skimmers and the even more insidious shimmers can easily steal your credit and debit card information when you swipe.
Finding a scamming Card Shimmer at gas station pic.twitter.com/AZF8ibLkCt
— Interesting As Fuck (@InterestingsAsF) May 14, 2023
Credit card skimmers and shimmers are illegal devices used by criminals to steal credit card information. They are designed to collect data from the magnetic stripe or chip of a credit card, which can then be used for fraudulent purposes.
- Credit Card Skimmers: Credit card skimmers are physical devices attached to legitimate card readers, such as those found at ATMs, gas pumps, or point-of-sale (POS) terminals. Skimmers are often designed to blend in seamlessly with the original machine, making them difficult to detect. When a card is swiped or inserted into the compromised device, the skimmer collects the card’s data, including the card number, expiration date, and sometimes the cardholder’s name. Criminals can later retrieve the skimming device and use the stolen data to create counterfeit cards or make unauthorized transactions. Getting inside ATMs is difficult, so ATM skimmers sometimes fit over existing card readers. Most of the time, the attackers also place a hidden camera somewhere in the vicinity in order to record personal identification numbers, or PINs, used to access accounts. The camera may be in the card reader, mounted at the top of the ATM, or even in the ceiling.
- Credit Card Shimmers: Credit card shimmers are more advanced and harder to detect compared to skimmers. Shimmers are typically thin, wafer-like devices that can be inserted into the card slot of a payment terminal, specifically targeting chip-based cards. Shimmers are designed to intercept and collect data from the card’s EMV (Europay, Mastercard, and Visa) chip. When a card is inserted into the compromised terminal, the shimmer reads the card’s information, including the encrypted data stored on the chip. The criminal can later retrieve the shimmer and use the stolen information to create cloned cards.
It’s important to note that shimmers are more prevalent in regions where chip-based credit cards are commonly used, as they exploit the vulnerabilities in chip card technology. They are less effective against contactless payment methods like Near Field Communication (NFC), which use different encryption protocols.
Both skimmers and shimmers aim to obtain sensitive credit card data without the cardholder’s knowledge. Criminals may then use the stolen information for various fraudulent activities, such as making unauthorized purchases or selling the data on the black market.
To protect yourself from credit card skimming and shimming:
- Inspect card readers: Before using an ATM or card reader, examine it for any signs of tampering, loose parts, or unusual attachments. If anything seems suspicious or doesn’t look right, avoid using it and report it to the establishment or authorities.
- Use secure and trusted terminals: Whenever possible, use well-known and reputable payment terminals or ATMs. Those located in secure areas or monitored by security personnel are less likely to be compromised.
- Monitor your account: Regularly review your credit card and bank account statements for any unauthorized transactions. If you notice any suspicious activity, report it to your financial institution immediately.
- Protect your PIN: When entering your PIN at an ATM or point-of-sale terminal, shield the keypad from prying eyes or hidden cameras. Be cautious of anyone who appears to be watching or acting suspiciously nearby.
- Use contactless payments: Consider using contactless payment methods like mobile wallets (e.g., Apple Pay, Google Pay) or contactless credit cards. These methods use encrypted tokens and dynamic transaction codes, making them less susceptible to skimming and shimming attacks.
Here’s how to protect yourself from these rare, but nasty, attacks.
- When approaching an ATM:
- Check for signs of tampering at the top, near speakers, the screen, card reader, and keyboard.
- Look for differences in color, material, graphics alignment, or anything that looks out of place.
- If anything seems suspicious, avoid using that ATM.
- At the bank:
- Compare neighboring ATMs for obvious differences.
- If you notice discrepancies, don’t use either ATM and report the tampering to your bank.
- For example, if one ATM has a flashing card entry and the other has a plain slot, it could indicate tampering.
- Pay attention to the keyboard:
- If it feels too thick or off-center, there might be a PIN-snatching overlay.
- Look for other signs of tampering, like holes that could hide a camera or bubbles from poor attachment.
- Test for stability and secure construction:
- Push and pull various parts of the ATM to check for loose or protruding components.
- Verify the keyboard is securely attached and a single piece.
- If anything moves or feels unstable, be cautious and avoid using the ATM.